Vault: Managed Database Credentials
with Hashicorp Vault
About Me
- Che Chia Chang
- SRE @ Maicoin
- Microsoft MVP
- chechia.net

相關資源
大綱
- DB 帳號密碼管理的難題
- Vault DB secret engine
- Demo 1 需要時自動產生資料庫帳號密碼
- Vault auth method 第三方認證身份
- Demo 2 github login and auth
- 程式化權限管理與稽查
- Demo 3 terraform 設定 vault 與 DB secret engine
- (看時間) monitoring / audit
DB 帳號密碼管理的難題
- 認證(Authentication)
- 密碼保管與暴露
- 授權(Authorization)
- 密碼更新
Authentication 認證
you are who you say you are
Authorization 授權
you are allowed to do what you are trying to do
User Story
- 一個app,為app設定了一個資料庫
- 資料庫存放app資料,只有app能存取資料
- 使用帳號密碼認證,app可以存取資料庫
app(username=app, password) > DB
DB > hi, app!
難題/認證
對於資料庫來說,username=app的人,就是app
- 有帳號密碼是否就相信他是app?
- 有沒有賬號密碼以外的方式確認app的身份?
難題/認證/密碼保管與暴露
- dba 需要開發db,手上有admin帳號密碼
- 資安風險
- 開發機器安裝惡意軟體/側錄密碼
- 帳號密碼被竊取
- 員工分開私人與公司電腦
難題/認證/密碼暴露
- 更嚴謹的身份確認,更難被破解
- ex Client Certificate Authentication
- 安全的存放密碼,避免密碼暴露
- 更好的做法
- 不要存放密碼,卻能使用密碼??
- 放在 Vault 裡面
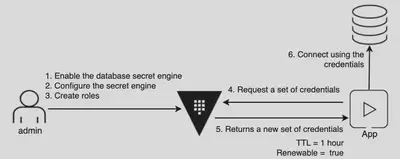

- 需要時自動產生DB使用者密碼
- 短效期使用者與密碼 ex 1hr
- 不延展自動到期,刪除使用者
- 未完成工作可以自動延展
- app可以一直取得新使用者與密碼
User Story (v2)
- 只有 vault 有 admin 密碼
- user 需要時,vault 動態產生短效期使用者與密碼
- 效期到自動刪除
- 使用 vault library 程式化連線 db
- 不在開發機器上存密碼
- 不手動輸入密碼
Vault DB secret engine 支援,沒支援可以自己寫 plugin
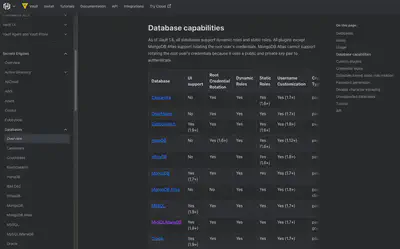
Demo 1: Vault DB secret engine
Setup
git clone git@github.com:chechiachang/vault-playground.git
cd vault-playground/deploy/04-docker-and-db/
docker-compose up -d
docker ps
docker exec -it 04-docker-and-db-mariadb_1-1 bash
docker exec -it 04-docker-and-db-vault_1-1 sh
apk update && apk add mysql-client
mysql -h mariadb_1 -u root -p
Demo 1: Vault DB secret engine
// Connect to docker vault
export VAULT_ADDR=http://127.0.0.1:8200
vault status
vault login
vault secrets list
// Configure secret engine database (terraform)
vault secrets list
vault policy list
cd usage/03-terraform-lives
terragrunt init
terragrunt apply
Demo 1: Vault DB secret engine
Use database secret engine
// root configure (already done by terraform)
vault secrets list
vault list localhost_mariadb/config
vault read localhost_mariadb/config/localhost_mariadb
vault list localhost_mariadb/roles
vault read localhost_mariadb/roles/database_admin
vault policy list
vault policy read dba
// create token for dba (will automatically done in Demo 2)
vault token create -policy=dba -display-name=dba \
-ttl=1h -use-limit=5
Demo 1: Vault DB secret engine
// auth as dba
vault login
vault policy list
vault read localhost_mariadb/creds/database_admin
mysql --sql -h localhost -u <username> -p
// do dba things
show databases;
select user from mysql.user;
...
exit
解決存放與取用,回到難題/認證
對於資料庫來說,username=app的人,就是app
- 有帳號密碼是否就相信他是app?
- 有沒有賬號密碼以外的方式確認app的身份?
Vault 的解決方案
難題/認證/Vault Auth method
Vault 仰賴外部可信第三方(trusted authority)
- user/app 透過第三方動態取得合法的身份
- aws / azure / gcp iam role / github / saml / LDAP …
開發機器上沒有密碼,就不會因為機器被駭/側錄,造成密碼洩漏
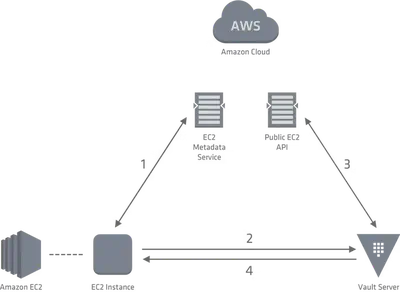
難題/認證/Vault Auth method/AWS
- IAM auth method
- EC2 auth method
- 透過 AWS API 去確認身份
- 登入的 aws user / 合法的 iam role
- vault 透過 aws api 去核對身份
- 核對正確,vault 提供短期 database credential 給 user / app
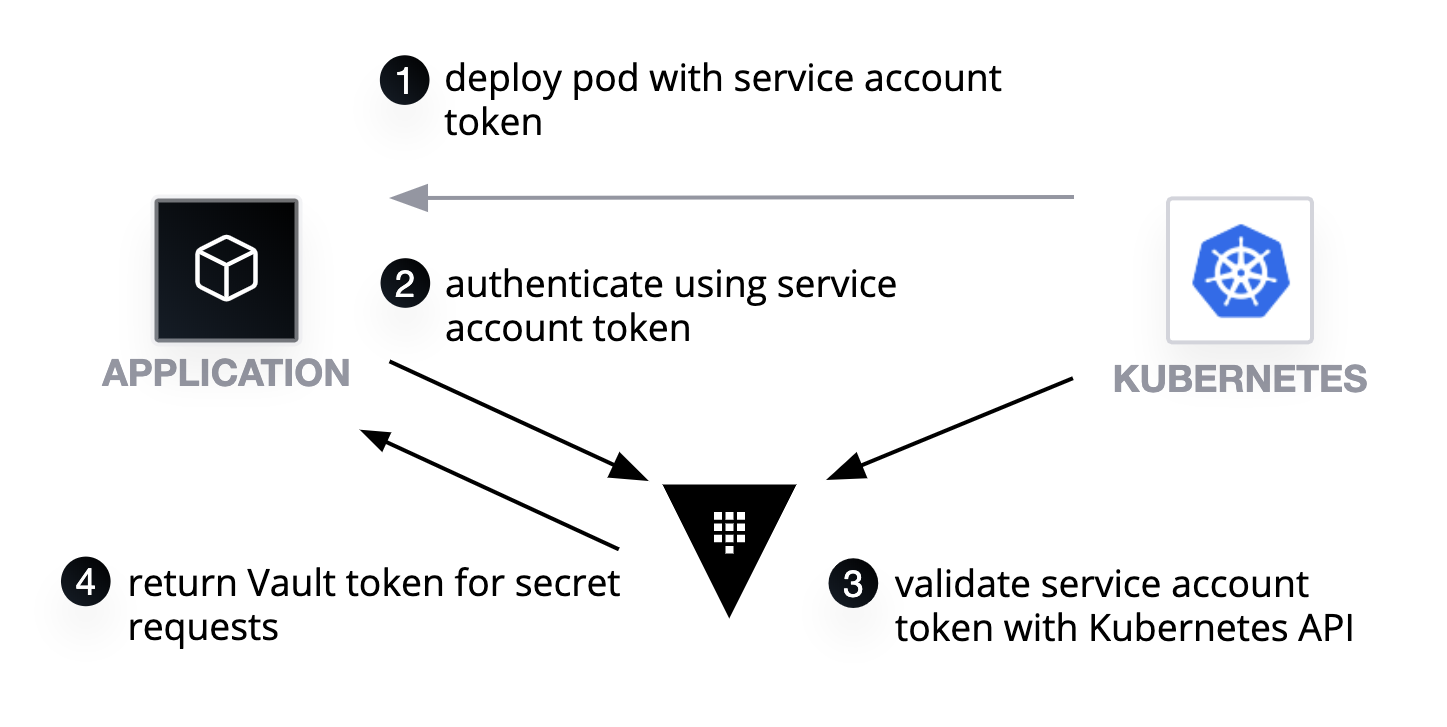
app 跑在 Kubernetes 上,使用 Service Account 做認證
使用 Vault auth method,信任第三方取得身份 從雙方查核,變成三方查核
User Story (v3)
- 只做一次:Vault 設定 DB secret engine
- user 本機不存放 DB 帳號密碼
- user/app 透過 Vault auth method
- user aws iam role
- app k8s service account
- user/app可以存取vault中的db帳號密碼
app > trusted authority
app < (identity) < trusted authority
app > (identity) > vault > trusted authority
app < (DB credential) < vault>
Demo 2: Auth method
https://developer.hashicorp.com/vault/docs/auth/github
// root
vault policy list
vault policy read sre
vault list auth/github-chechia-net/map/users
vault read auth/github-chechia-net/map/users/chechiachang
vault list auth/github-chechia-net/map/teams
vault read auth/github-chechia-net/map/teams/sre
vault auth help github-chechia-net
// user (github login)
vault login -method=github -path=github-chechia-net token=$TOKEN
vault read localhost_mariadb/creds/database_admin
Demo 2: Auth method
https://developer.hashicorp.com/vault/docs/auth/aws
// User login Public Cloud
aws-vault exec dev -- vault login -method=aws -path=aws=sre
gcloud ... vault login -method=gcp -path=gcp=sre
az login ... vault login -method=azure -path=azure=sre
// app login k8s
難題/認證/Vault Auth method/Kubernetes
app > sa -> k8s api server -> vault -> DB
- 使用 k8s vault injector
- app 跑在 Pod,Pod 取得 k8s service account 短期 jwt token
- app 透過 jwt token 給 vault 聲稱自己是 app
- vault 使用 jwt token 與 k8s api server 核對 pod service account
- k8s 核對成功,vault 認為 app 是 k8s 中的 app
- vault 提供短期 database credential 給 app
- app 使用短期 database credential 存取資料庫
難題/認證/Vault Auth method/小結
- 本地存放 password 的風險
- 如果有公有雲,存放雲端服務
- 通過檢驗且合規的安全系統
- 如果是地端,使用 vault 來管理帳號密碼
- 存放 admin
- 動態產生 db user
User Story (v?)
需求會一直改變
- app 存取資料,變成
- app + admin + metabase 不同權限
難題/授權
MySQL 為例,使用 sql 管理授權
user based access control
grant write on mydb.* to app@'%'
grant all on mydb.* to admin@'%'
grant read on mydb.* to metabase@'%'
role based access control
create role myrole;
grant all on mydb.* to myrole;
grant myrole to app@'%';
難題/授權/Scale up
- Scale up,100 個 user x 100 個 database
- 權限變更難 review
- 變更授權的admin user權力很大,如何存放管理
難題/授權/Scale up
resource "mysql_role" "myrole" {
for_each = var.roles
name = each.key
}
resource "mysql_grant" "developer" {
for_each = var.roles
role = each.key
database = each.value.database
privileges = each.value.privilleges // ["SELECT", "UPDATE"]
}
難題/授權/PR Review
- Terraform 管理 MySQL 授權
- Terraform 有比較好嗎?
- 程式化設定
- Reviewable / Testable code
- 請見從零開始學Terraform手把手入門
難題/授權/Automation
Vault 管理授權
- Or Vault + Terraform?
vault policy list
database_admin
database_readonly
database_write
vault policy read database_write
path "chechia-net-myapp/database/database" {
capabilities = ["create", "read", "update", "patch", "delete", "list"]
}
Demo 3: Terraform 設定 Vault 與 DB secret engine
// destroy
cd vault-playground/usage/03-terraform-lives
terragrunt destroy
cd vault-playground/deploy/04-docker-and-db/
docker-compose down
// create new
docker-compose up -d
docker ps
cd vault-playground/usage/03-terraform-lives
terragrunt apply
Demo 3: Terraform 設定 Vault 與 DB secret engine
- 程式化權限控管
- 一鍵設定環境
- CI/CD 測試
- fmt, lint, unit test
- CI/CD 測試
- PR Review
- 一鍵設定環境
- Automation plan,apply
- 避免人工操作的失誤與風險
- DBA 不用密碼或 login,因為根本不連 prod DB
- incident 一鍵 roll back
總結
- Vault DB secret engine
- 管理資料庫帳號密碼
- 動態產生 db user
- Vault auth method
- 第三方認證身份
- Github / AWS IAM Role / Kubernetes Service Account
- Vault + Terraform
- 程式化權限控管
- PR Review
- Automation plan,apply